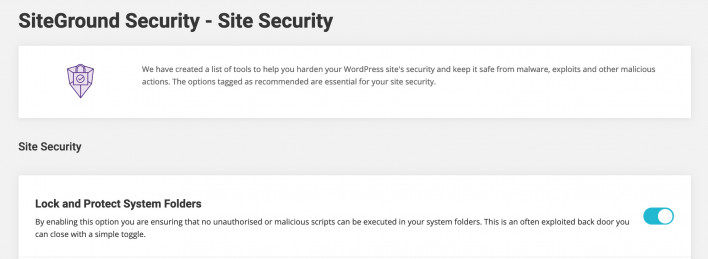
Site Security
This page has a list of tools to help you harden your WordPress site’s security and keep it safe from malware, exploits and other malicious actions. By default, all options are enabled.
Lock and Protect System Folders
By enabling this option an .htaccess file is placed in your WordPress’ system folders, preventing the execution of unauthorized or suspicious scripts from being executed from them.
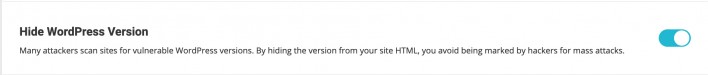
Hide WordPress Version
By enabling this option the information about your WordPress version is removed from your site’s HTML code. This prevents any potential attackers that target specific WordPress versions from marking your website for mass attacks.
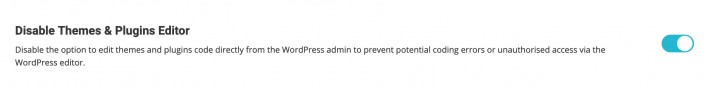
Disable Themes & Plugins Editor
This will remove the option to edit your website’s theme and plugins’ code from the WordPress admin panel, which will prevent any unauthorized access via the WordPress editor.
Disable XML-RPC
XML-RPC was designed as a protocol enabling WordPress to communicate with third-party systems but it has been used in a number of exploits. Unless you specifically need to use it, it is recommended that XML-RPC is always disabled.
Force HTTP Strict-Transport-Security (HSTS)
HSTS (HTTP Strict-Transport-Security) is a response header. It allows the website to tell browsers that it should only be accessed using HTTPS, instead of using HTTP. If a website accepts a connection through HTTP and redirects to HTTPS, visitors may initially communicate with the non-encrypted version of the site before being redirected. This creates an opportunity for a “man-in-the-middle” attack. The redirect could be exploited and regular visitors to be redirected to a malicious site instead of the secure version of the origin.
Disable RSS and ATOM Feeds
RSS and ATOM feeds allow for content scraping which can be used in attacks on your website. If you do not have any readers using RSS feeds then you should enable this option.
Advanced XSS Protection
Cross-Site Scripting (XSS) attacks are a type of injection, in which malicious scripts are injected into otherwise benign and trusted websites. This feature will protect your website against these types of attacks by inserting additional lines inside your website’s .htaccess file.
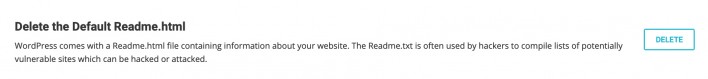
Delete the Default Readme.html
This will delete the default readme.html file that comes with your WordPress core files. The file can be used by attackers to compile lists of potentially vulnerable sites which can be hacked or attacked.